In new 3850 switch model, you can take packet captures within switch itself (no longer required to port span by connecting a pc which is running wireshark). This switch model comes with embeded wireshark feature.
You should have IOS-XE 3.3.0 or later images to have this feature. Here is few things to remember when taking wireless packet captures
* The only form of wireless capture is a CAPWAP tunnel capture.
* When capturing CAPWAP tunnels, no other interface types can be used as attachment points on the same capture point.
* Capturing multiple CAPWAP tunnels is supported.
* Core filters are not applied and should be omitted when capturing a CAPWAP tunnel.
* To capture a CAPWAP data tunnel, each CAPWAP tunnel is mapped to a physical port and an appropriate ACL will be applied to filter the traffic.
* To capture a CAPWAP non-data tunnel, the switch is set to capture traffic on all ports and apply an appropriate ACL to filter the traffic.
Here how you can get a packet capture from it.
I have one AP connected to my 3850 & it uses “Ca0″ interface to terminate CAPWAP tunnel on to it. So we will capture the packets going in/out form this interface. There are two active clients connected to this AP while taking the packet capture.
3850-1#sh capwap summary CAPWAP Tunnels General Statistics: Number of Capwap Data Tunnels = 1 Number of Capwap Mobility Tunnels = 0 Number of Capwap Multicast Tunnels = 0 Name APName Type PhyPortIf Mode McastIf ------ -------------------------------- ---- --------- --------- ------- Ca0 L3502-1 data Gi1/0/1 unicast - Name SrcIP SrcPort DestIP DstPort DtlsEn MTU Xact ------ --------------- ------- --------------- ------- ------ ----- ---- Ca0 10.15.4.255 5247 10.15.5.253 48645 No 1449 0 3850-1#show wireless client summary Number of Local Clients : 2 MAC Address AP Name WLAN State Protocol -------------------------------------------------------------------------------- 04f7.e4ea.5b66 L3502-1 17 UP 11n(5) 2c54.2dea.f4ea L3502-1 17 UP 11a
There are 3 basic steps involve in capturing process.
1. Define your source interface (Ca0 interface in this example)
3850-1#monitor capture ? WORD Name of the Capture 3850-1#monitor capture MY_CAP ? access-list access-list to be attached buffer Buffer options class-map class name to attached clear Clear Buffer control-plane Control Plane export Export Buffer file Associated file attributes interface Interface limit Limit Packets Captured match Describe filters inline start Enable Capture stop Disable Capture vlan Vlan 3850-1#monitor capture MY_CAP interface ? GigabitEthernet GigabitEthernet IEEE 802.3z TenGigabitEthernet Ten Gigabit Ethernet Vlan Catalyst Vlans capwap Capwap-Tunnel range interface range command 3850-1#monitor capture MY_CAP interface capwap ? WORD Capwap ID List Eg. 0-10, 15 3850-1#monitor capture MY_CAP interface capwap 0 ? both Inbound and outbound packets in Inbound packets out Outbound packets 3850-1#monitor capture MY_CAP interface capwap 0 both
2. Set your filter for the capture (for CAPWAP interfaces no filtering option supported). To filtering you can use ACL or “match” statements as shown below. Note that I have not used it for this example.
3850-1#monitor capture MY_CAP match ? any all packets ipv4 IPv4 packets only ipv6 IPv6 packets only mac MAC filter configuration 3850-1#monitor capture MY_CAP match ipv4 ? A.B.C.D/nn IPv4 source Prefix <network>/<length>, e.g., 192.168.0.0/16 any Any source prefix host A single source host protocol Protocols 3850-1#monitor capture MY_CAP match ipv4 any ? A.B.C.D/nn IPv4 destination Prefix <network>/<length>, e.g., 192.168.0.0/16 any Any destination prefix host A single destination host 3850-1#monitor capture MY_CAP match ipv4 any any 3850-1#monitor capture MY_CAP access-list ? WORD access-list name 3850-1#monitor capture MY_CAP access-list ACL ? buffer Buffer options control-plane Control Plane file Associated file attributes interface Interface limit Limit Packets Captured vlan Vlan <cr>
3. Define your destination (you can use internal flash or USB flash as the file destination)
3850-1#monitor capture MY_CAP file location ? crashinfo-1: Location of the pcap file crashinfo: Location of the pcap file flash-1: Location of the pcap file flash: Location of the pcap file stby-usbflash0: Location of the pcap file usbflash0-1: Location of the pcap file usbflash0-2: Location of the pcap file usbflash0: Location of the pcap file 3850-1#monitor capture MY_CAP file location flash:MY_CAP.pcap ? access-list access-list to be attached buffer-size Size of temporary buffer (to reduce packet loss) class-map class name to attached control-plane Control Plane interface Interface limit Limit Packets Captured match Describe filters inline ring Store the contents in a circular file chain size Size of the file(s) vlan Vlan <cr> 3850-1#monitor capture MY_CAP file location flash:MY_CAP.pcap buffer-size ? <1-100> Buffer size in MB : Min 1 : Max 100 3850-1#monitor capture MY_CAP file location flash:MY_CAP.pcap buffer-size 10 ? access-list access-list to be attached class-map class name to attached control-plane Control Plane interface Interface limit Limit Packets Captured match Describe filters inline ring Store the contents in a circular file chain size Size of the file(s) vlan Vlan <cr> 3850-1#monitor capture MY_CAP file location flash:MY_CAP.pcap buffer-size 10
4. You can activate/de-activate the packet capture as shown below. I have left it running for 30s-60s & then stopped
3850-1#monitor capture MY_CAP start . . . 3850-1#monitor capture MY_CAP stop
As you can see file is available in 3850′s flash.
3850-1#dir Directory of flash:/ 85193 -rwx 2097152 Oct 29 2013 09:18:33 +11:00 nvram_config 85186 -rw- 257016048 Oct 15 2013 10:46:31 +11:00 cat3k_caa-universalk9.SPA.03.03.00.SE.150-1.EZ.bin 85188 -rw- 1214 Oct 8 2013 09:16:25 +11:00 packages.conf.00- 61955 -rw- 5430 Nov 12 2013 13:28:00 +11:00 MY_CAP.pcap
You can open it using Wireshark application or view from the switch itself(it is always good to analyze this using wireshark application as if you do it on swith, it can consume switch resources like CPU/memory) . Here is how you can view it on switch itself.
3850-1#show monitor capture file flash:MY_CAP.pcap 1 0.000000 x.y.104.252 -> 224.0.0.2 HSRP Hello (state Standby) 2 0.288031 x.y.104.251 -> 224.0.0.2 HSRP Hello (state Active) 3 1.899999 10.15.4.255 -> 10.15.5.253 CAPWAP CAPWAP-Control - Primary Discovery Response 4 1.899999 10.15.4.255 -> 10.15.5.253 CAPWAP CAPWAP-Control - Primary Discovery Response 5 2.656008 x.y.104.252 -> 224.0.0.2 HSRP Hello (state Standby) 6 2.961992 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 7 2.961992 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 8 2.961992 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 9 2.967988 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 10 2.967988 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 11 2.967988 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 12 2.972993 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 13 3.099985 x.y.104.251 -> 224.0.0.2 HSRP Hello (state Active) 14 4.455015 2c:3f:38:2b:57:00 -> 2c:3f:38:2b:57:00 WLCCP U, func=UI; SNAP, OUI 0x004096 (Cisco Wireless (Aironet) L2), PID 0x0000 15 4.456022 2c:3f:38:2b:57:00 -> 2c:3f:38:2b:57:00 WLCCP U, func=UI; SNAP, OUI 0x004096 (Cisco Wireless (Aironet) L2), PID 0x0000 16 5.071987 x.y.104.252 -> 224.0.0.2 HSRP Advertise (state Passive) 17 5.278037 x.y.104.252 -> 224.0.0.2 HSRP Hello (state Standby) 18 5.911992 x.y.104.251 -> 224.0.0.2 HSRP Hello (state Active) 19 7.406021 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 20 7.411026 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 21 7.411026 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 22 7.417022 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 23 7.422027 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 24 7.428023 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 25 8.266029 x.y.104.252 -> 224.0.0.2 HSRP Hello (state Standby) 26 8.684007 x.y.104.251 -> 224.0.0.2 HSRP Hello (state Active) 27 10.191976 2c:3f:38:2b:57:00 -> 2c:3f:38:2b:57:00 WLCCP U, func=UI; SNAP, OUI 0x004096 (Cisco Wireless (Aironet) L2), PID 0x0000 28 11.266029 x.y.104.252 -> 224.0.0.2 HSRP Hello (state Standby) 29 11.360033 x.y.104.251 -> 224.0.0.2 HSRP Hello (state Active) 30 12.763013 10.11.255.40 -> x.y.104.190 SKINNY CallStateMessage 31 12.763013 10.11.255.40 -> x.y.104.190 SKINNY SelectSoftKeysMessage 32 12.769009 x.y.104.190 -> 10.11.255.40 TCP 1036 > 2000 [ACK] Seq=1 Ack=37 Win=15840 Len=0 TSV=243324138 TSER=1861909984 33 12.769009 10.11.255.40 -> x.y.104.190 SKINNY 0x00000145 (Unknown) 0x00000144 (Unknown) 0x0000014A (Unknown) SetLampMessage SetRingerMessage 34 12.771008 x.y.104.190 -> 10.11.255.40 TCP 1036 > 2000 [ACK] Seq=1 Ack=65 Win=15840 Len=0 TSV=243324138 TSER=1861909984 35 12.777004 x.y.104.190 -> 10.11.255.40 TCP 1036 > 2000 [ACK] Seq=1 Ack=289 Win=15840 Len=0 TSV=243324139 TSER=1861909988 36 13.717010 x.y.104.252 -> 224.0.0.2 HSRP Hello (state Standby) 37 13.836007 x.y.104.251 -> 224.0.0.2 HSRP Hello (state Active) 38 14.177984 00:00:00:00:00:00 -> 2c:3f:38:2b:57:00 IEEE 802.11 Probe Request, SN=0, FN=0, Flags=........ 39 15.023985 x.y.104.190 -> 10.11.255.40 SKINNY KeepAliveMessage 40 15.023985 10.11.255.40 -> x.y.104.190 SKINNY KeepAliveAckMessage 41 15.026991 x.y.104.190 -> 10.11.255.40 TCP 1036 > 2000 [ACK] Seq=13 Ack=301 Win=15840 Len=0 TSV=243324364 TSER=1861912240 42 15.171988 00:00:00:00:00:00 -> 2c:3f:38:2b:57:00 IEEE 802.11 Probe Request, SN=0, FN=0, Flags=........ 43 16.166983 00:00:00:00:00:00 -> 2c:3f:38:2b:57:00 IEEE 802.11 Probe Request, SN=0, FN=0, Flags=........ 44 16.392029 x.y.104.252 -> 224.0.0.2 HSRP Hello (state Standby) 45 16.667009 x.y.104.251 -> 224.0.0.2 HSRP Hello (state Active) 46 16.926990 10.15.5.253 -> 10.15.4.255 DTLSv1.0 Application Data 47 17.159980 00:00:00:00:00:00 -> 2c:3f:38:2b:57:00 IEEE 802.11 Probe Request, SN=0, FN=0, Flags=........ 48 17.573020 x.y.104.190 -> 10.11.255.40 SKINNY SoftKeyEventMessage 49 17.573020 10.11.255.40 -> x.y.104.190 SKINNY SetRingerMessage 50 17.573020 10.11.255.40 -> x.y.104.190 SKINNY SetSpeakerModeMessage 51 17.573020 10.11.255.40 -> x.y.104.190 SKINNY SetLampMessage 52 17.577017 x.y.104.190 -> 10.11.255.40 TCP 1036 > 2000 [ACK] Seq=37 Ack=329 Win=15840 Len=0 TSV=243324619 TSER=1861914780
If you want to see specific frame in detail (eg Frame 38) you can do that as well.
3850-1#show monitor capture file flash:MY_CAP.pcap detailed | beg Frame 38 Frame 38: 122 bytes on wire (976 bits), 122 bytes captured (976 bits) Arrival Time: Nov 12, 2013 03:04:08.970942000 UTC Epoch Time: 1384225448.970942000 seconds [Time delta from previous captured frame: 0.341977000 seconds] [Time delta from previous displayed frame: 0.341977000 seconds] [Time since reference or first frame: 14.177984000 seconds] Frame Number: 38 Frame Length: 122 bytes (976 bits) Capture Length: 122 bytes (976 bits) [Frame is marked: False] [Frame is ignored: False] [Protocols in frame: eth:ip:udp:capwap:wlan] Ethernet II, Src: cc:ef:48:9b:e0:45 (cc:ef:48:9b:e0:45), Dst: 58:bf:ea:b6:56:c3 (58:bf:ea:b6:56:c3) Destination: 58:bf:ea:b6:56:c3 (58:bf:ea:b6:56:c3) Address: 58:bf:ea:b6:56:c3 (58:bf:ea:b6:56:c3) .... ...0 .... .... .... .... = IG bit: Individual address (unicast) .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) Source: cc:ef:48:9b:e0:45 (cc:ef:48:9b:e0:45) Address: cc:ef:48:9b:e0:45 (cc:ef:48:9b:e0:45) .... ...0 .... .... .... .... = IG bit: Individual address (unicast) .... ..0. .... .... .... .... = LG bit: Globally unique address (factory default) Type: IP (0x0800) Internet Protocol, Src: 10.15.5.253 (10.15.5.253), Dst: 10.15.4.255 (10.15.4.255) Version: 4 Header length: 20 bytes Differentiated Services Field: 0xc0 (DSCP 0x30: Class Selector 6; ECN: 0x00) 1100 00.. = Differentiated Services Codepoint: Class Selector 6 (0x30) .... ..0. = ECN-Capable Transport (ECT): 0 .... ...0 = ECN-CE: 0 Total Length: 108 Identification: 0xa865 (43109) Flags: 0x02 (Don't Fragment) 0... .... = Reserved bit: Not set .1.. .... = Don't fragment: Set ..0. .... = More fragments: Not set Fragment offset: 0 Time to live: 255 Protocol: UDP (17) Header checksum: 0xb341 [correct] [Good: True] [Bad: False] Source: 10.15.5.253 (10.15.5.253) Destination: 10.15.4.255 (10.15.4.255) User Datagram Protocol, Src Port: 48645 (48645), Dst Port: 5247 (5247) Source port: 48645 (48645) Destination port: 5247 (5247) Length: 88 Checksum: 0x0000 (none) [Good Checksum: False] [Bad Checksum: False] Control And Provisioning of Wireless Access Points Preamble Version: 0 Type: CAPWAP Header (0) Header Header Length: 4 Radio ID: 0 Wireless Binding ID: IEEE 802.11 (1) Header flags 1... .... . = Payload Type: Native frame format (see Wireless Binding ID field) .0.. .... . = Fragment: Don't Fragment ..0. .... . = Last Fragment: More fragments follow ...1 .... . = Wireless header: Wireless Specific Information is present .... 0... . = Radio MAC header: No Radio MAC Address .... .0.. . = Keep-Alive: No Keep-Alive .... ..00 0 = Reserved: Not set Fragment ID: 0 Fragment Offset: 0 Reserved: 0 Wireless length: 4 Wireless data: 00000000 Wireless data ieee80211 Frame Info: 00000000 Wireless data ieee80211 RSSI (dBm): 0 Wireless data ieee80211 SNR (dB): 0 Wireless data ieee80211 Data Rate (Mbps): 0 Padding for 4 Byte Alignement: 000000 IEEE 802.11 Probe Request, Flags: ........ Type/Subtype: Probe Request (0x04) Frame Control: 0x0040 (Swapped) Version: 0 Type: Management frame (0) Subtype: 4 Flags: 0x0 .... ..00 = DS status: Not leaving DS or network is operating in AD-HOC mode (To DS: 0 From DS: 0) (0x00) .... .0.. = More Fragments: This is the last fragment .... 0... = Retry: Frame is not being retransmitted ...0 .... = PWR MGT: STA will stay up ..0. .... = More Data: No data buffered .0.. .... = Protected flag: Data is not protected 0... .... = Order flag: Not strictly ordered Duration: 0 Destination address: 2c:3f:38:2b:57:00 (2c:3f:38:2b:57:00) Source address: 00:00:00:00:00:00 (00:00:00:00:00:00) BSS Id: 2c:3f:38:2b:57:00 (2c:3f:38:2b:57:00) Fragment number: 0 Sequence number: 0 IEEE 802.11 wireless LAN management frame Tagged parameters (40 bytes) Vendor Specific: 00:40:96: Aironet Unknown Tag Number: 221 (Vendor Specific) Tag length: 9 Vendor: 00:40:96 Aironet IE type: Unknown (37) Aironet IE data: 017ae93ff1 Vendor Specific: 00:40:96: Aironet Unknown Tag Number: 221 (Vendor Specific) Tag length: 27 Vendor: 00:40:96 Aironet IE type: Unknown (37) Aironet IE data: 00012c542deaf4ea0101270095007ae5c1abf09002c5c9
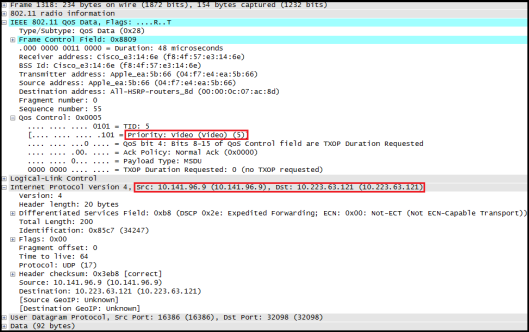
You can copy these file from switch Flash to wherever you wanted. Here is the few screenshot of this wireshark capture.
3850-1#copy flash tftp: Source filename [MY_CAP.pcap]? Address or name of remote host []? x.y.13.2 Destination filename [MY_CAP.pcap]? !!!!!!!!!!!!!!!!! 3908147 bytes copied in 21.010 secs (186014 bytes/sec)
Here is a good reference for wired interface packet capturing using the same feature.
Refer this config guide (for IOS-XE 3.3.0) section for the Wireshark configuration of this version.
Hope you will enjoy this new feature available for easy troubleshooting.